Download catalogue of technologies
ISP Obfuscator
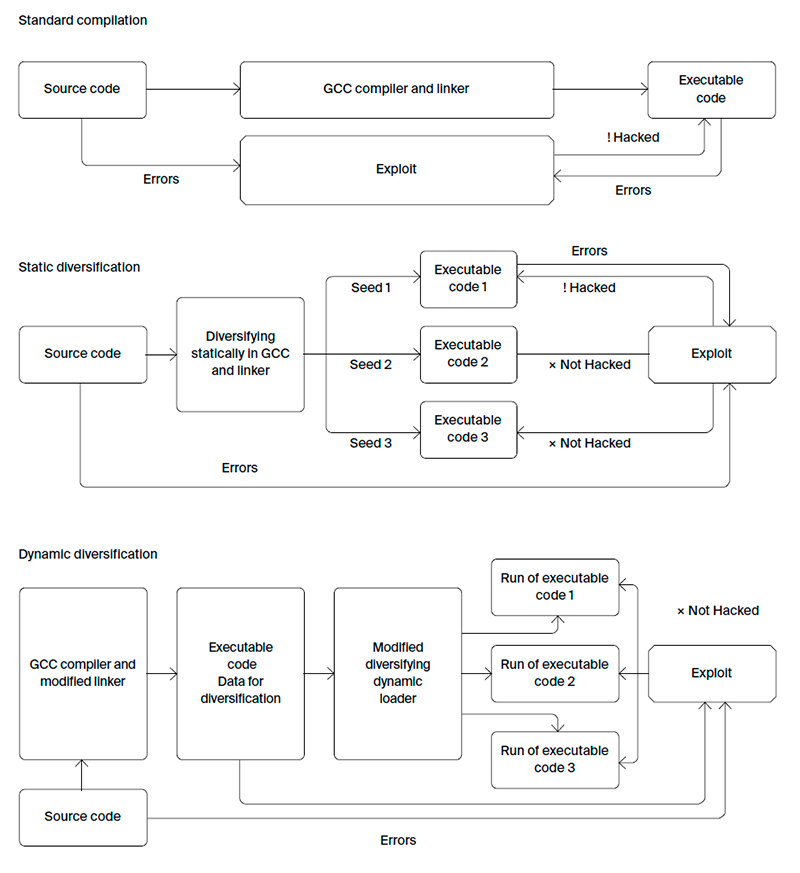
Obfuscator is a set of technologies to prevent mass exploitation of vulnerabilities resulting from errors or backdoors. In case a hacker has attacked one of the devices that has a certain software installed, the rest will remain protected by changes to the code that the tool made.
Features and advantages
Obfuscator protects a software system from mass exploitation of vulnerabilities using various code diversification methods and allows compiling a full OS distribution.
ISP Obfuscator provides:
- Fine-tuning the balance of obfuscation level and performance (when protecting against reverse engineering). The minimum speed degradation is 1.2 times, the maximum is 8 times.
- Full automation (no need to change the program source code or to spend efforts for build system integration).
- Based on the GCC compiler, which allows correctly building the full OS source code.
- The original control flow integrity technique (CFI), which successfully counteracts most of code reuse attacks (ROP, JOP, ret-to-libc, etc.). The implemented CFI support within the GCC compiler shows the average slowdown of about 2% on the SPEC CPU2006 test suite, which is noticeably lower than that of the traditional methods.
- Two diversification approaches:
Dynamic code diversification at program startup. It is used when the customer needs the same binary code deployed on all devices (for example, because of the certification procedure). This method allows shuffling up to 98% of code with a slight increase in size and a performance degradation of about 1.5%. The obfuscator provides the following advantages over the similar products:
- Shuffling with function granularity (as opposed to ASLR and Pagerando technologies that randomize only large blocks of code);
- Shuffling functions throughout the full OS code except the kernel, and avoiding conflicts with the antivirus software (compared to the Selfrando technology developed for the Tor Browser);
- the binary code size does not increase (which is particularly important for the Internet of things use case);
- performance degradation is close to zero;
- an extended set of diversifying transformations can be applied and more flexibly customized, as the required operations are performed within the compiler during build time, as opposed to working at link time.
- performs also Control Flow Integrity (CFI).
- Conflict-free combination with other software protection tools (including the ASLR system mechanism).
Static code diversification. During each separate compilation, depending on the specified key, the new executable file is created. This approach has the following advantages:
Who is Obfuscator target audience?
- Developers of specialized operating systems.
- Application software developers.
Obfuscator deployment stories
ISP Obfuscator is deployed in the Zirkon OS, which is used by the Ministry of Foreign Affairs and the Border Guard Service of the Federal Security Service of Russia.
System requirements
Obfuscator is a universal product that can be adapted to many system requirements. The production version is currently running on a Linux-based OS (version 2.6 and higher) with the Intel x86/x86-64 architecture support.
Obfuscator workflow
Developer/Participant
Back to the list of technologies of ISP RAS 


