ISP Obfuscator. Code obfuscation to protect against vulnerability exploitation
ISP Obfuscator
ISP Obfuscator is based on long-term research that ISP RAS started as early as 2002.
The obfuscation technology grew up from basic research to industrial deployment. It is covered by dozens of publications and two PhD theses during these years.
ISP Obfuscator is dedicated to protect software products in various scenarios:
- prevent reverse engineering: make algorithms and data structures hard to understand even to well-equipped attacker;
- prevent patch-based exploit generation;
- secure identification of executable files through watermarking;
- mitigate vulnerability exploitation.
To achieve its objectives ISP Obfuscator provides a rich set of code transformations:
- replacement of local variables with globals, making fake dependencies between units or modules,
- control flow graph (CFG) flattening to obscure code structure and algorithm logic,
- function cloning that blurs codebase and introduces fake independently looking modules,
- function weaving when multiple functions are inlined and their bodies interwoven to obscure call graph,
- hiding function calls to obscure program structure and decomposition into modules,
- creating irreducible CFG, thus introducing fake dependencies between code statements,
- constant data encryption to hide strings (such as URLs of the endpoints) or other values that can illuminate the logic of the program,
- injection of fake loops to impede analysis and debugging,
- constant folding is a lightweight alternative to constant encryption,
- injection of fake local variables and reordering of the true ones to hamper data flow analysis,
- reordering functions to prevent patch-based exploits.
ISP Obfuscator integrates with compilers to make those transformations transparent for developers. At the moment two compiler infrastructures are supported: LLVM and GCC.
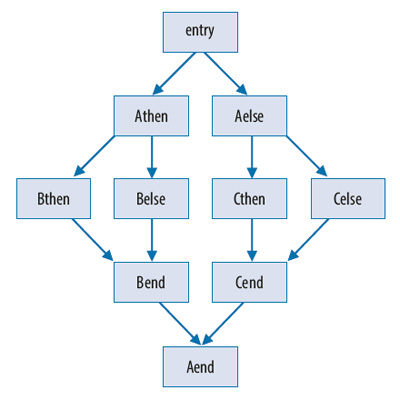
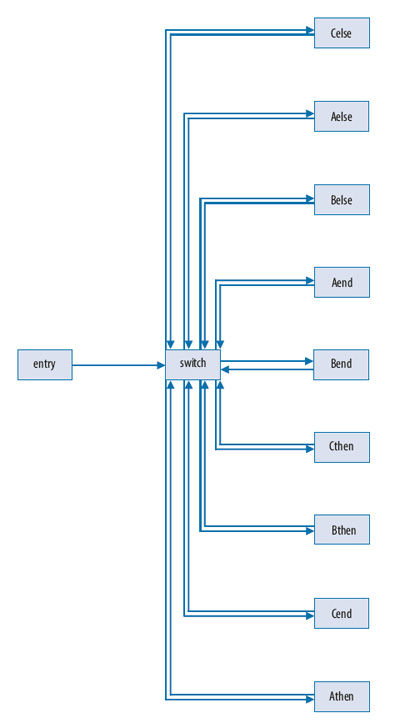
CFG Flattening
This is one of the most powerful obfuscating transformations that makes a function's CFG look completely different while preserving its overall behavior. The protective property of CFG flattening is based on the fact that the reverse transformation, recovery of basic blocks ordering, by means of static analysis is NPhard.
The pictures illustrate the CFG flattening transformation. The first one shows original CFG that contains several nested conditional branches. CFG after the transformation is flat, as depicted on the other image, and the logic of the original algorithm is completely obscured.
Performance Impact
Obfuscating transformations decrease program performance and increase size of application. Some of them (e.g. CFG flattening) can make performance 10 times as slower. Thanks to the wide spectrum of obfuscating transformations provided by ISP Obfuscator users can leverage protection while keeping the overhead reasonably small.
Using ISP Obfuscator for Exploit Mitigation
Programming errors and software backdoors can be exploited. Nowadays, there is a software monoculture when identical applications run on millions of computers. A single exploit may potentially hurt all users of a compromised program. Having same binary code in every installation makes large scale exploitation easy. To meet this global challenge ISP Obfuscator includes a tool mitigating such attacks.
The tool is based on GCC compiler. It implements transformations that diversify program code. Obfuscator generates diversified population of executable files. Having received one application instance an attacker can create an exploit but it wouldn't work for other instances due to unpredictable differences in binaries. The diversifying transformations are lightweight and the performance degradation is negligible.
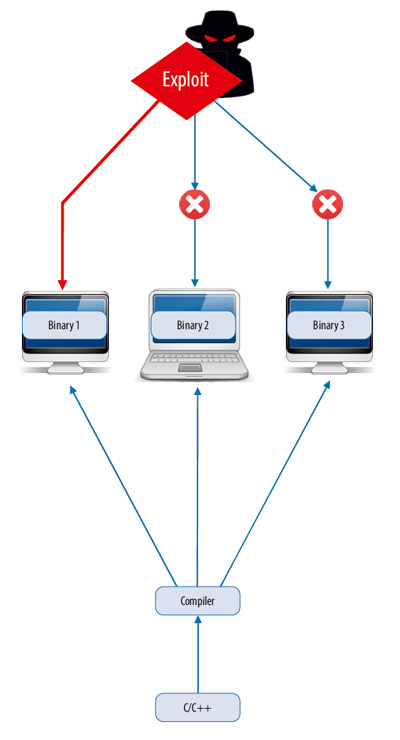
Our Customers
ISP Obfuscator is a part of Zircon OS – a special-purpose OS developed by Moscowbased Swemel company for government and federal agencies, including the Ministry of Foreign Affairs of the Russian Federation, Border Guard Service of Russia, Educational Centers of Russian Federal Security Service. Zircon operating systems and software have all the certificates required by the Federal Security Service and Federal Service for Technology and Export Control and can be used for processing highly sensitive information.
ISP Obfuscator (as a part of Zircon OS), based on GCC implements obfuscation techniques, provides injection of additional local variables into stack, local variables reordering, function reordering. These transformations lead to difference in stack sizes, shifting return address between instances. As a result, exploitation based on buffer overflow force attackers to guess data size individually for each instance, thus making massive exploits effectively impossible.
ROP Attack Mitigation
Rather than injecting a code to an executable ROP attacks utilize pieces of code of the application itself. Carefully selected code blocks called ROP gadgets are invoked through preciously handcrafted stack frames. Since such frames use return address to chain gadgets ROP attacks rely on the knowledge of the actual address of library or application functions. Modern operating systems use random addresses while they load executable modules to prevent fixed code locations, but if attackers can control system-wide random number seed or predict random numbers they can construct a ROP gadgets chain for the given compromised application.
The diversification effectively prevents ROP attacks even when random number generator is controlled by attackers. Due to functions reordering and variations in stack frame sizes addresses of ROP gadgets constructed from offsets of functions and system structures in one instance turn out to be unacceptable for constructing an exploit for a system that was not compromised.



