Download catalogue of technologies
ISP Crusher: a dynamic analysis toolset
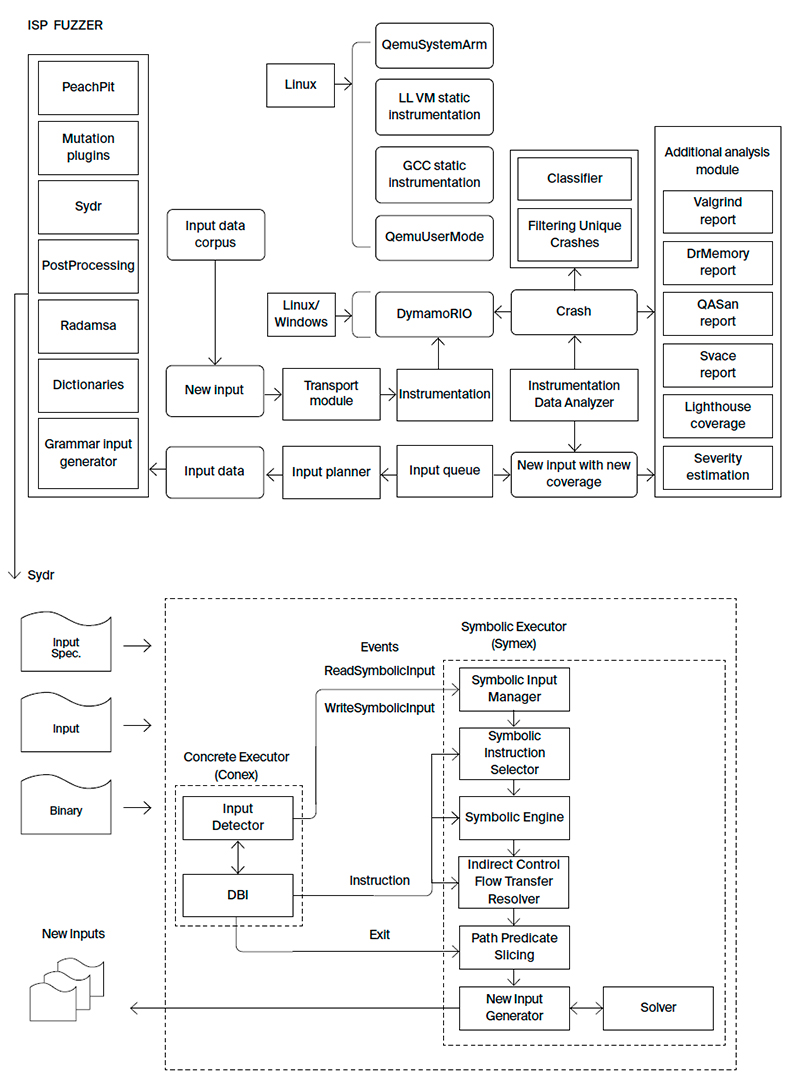
ISP Crusher is a toolset that combines various dynamic analysis approaches. It includes ISP Fuzzer, a fuzzing tool, and Sydr, an automatic test generation tool for complex programs. In the near future Crusher will also include the BinSide analyzer, another ISP RAS technology. Crusher allows organizing a development process that is fully compliant with GOST R 56939-2016 and other regulatory requirements of FSTEC of Russia.
ISP Fuzzer, a testing tool
ISP Fuzzer is a fuzzing tool that is essential for any software development phase, be it coding, testing, or deployment. The fuzzer finds program errors either with or without source code. It solves the same problems as its global competitors (Synopsys Codenomicon, beSTORM, Peach Fuzzer), but it is more convenient for Russian companies in the import substitution context.
ISP Fuzzer provides:
- Fuzzing various input data sources (files, command line arguments, standard input stream, environment variable arguments, network sockets, raw memory writes).
- Adding custom mutational transformations (for new input data generation and increasing fuzzing efficiency).
- Input data pre- and post-processing plugins for performing data transformations before feeding the data to the software being analyzed.
- Multicore and distributed parallel analysis support.
- Custom network plugins support allowing to interact with a client or a server and to send mutated data.
- Integration with other ISP RAS security development lifecycle tools, such as:
- using the Sydr dynamic symbolic execution analyzer for improving fuzzing efficiency;
- automated input data generation for triggering errors found by the BinSide static analysis tool;
- using Svace analyzer GUI to show a function call trace that resulted in a crash;
- using the ANTLR parser generator to create an input data corpora.
- Integration with the IDA PRO disassembler (exporting coverage data to the Lighthouse plugin for displaying covered basic blocks and showing the percentage of the coverage achieved).
- Analysis of client/server software working via stateless or stateful protocols.
- Support for describing scenarios for GUI software fuzzing.
- Broad support for embedded software fuzzing with partial emulation and symbolic execution.
- Adding user specified handlers to be called automatically for the newly generated input data.
- Running dynamic analyzers on generated input (Valgrind, DrMemory, QASan).
- Easy extension via adding new analysis algorithms to the existing infrastructure as well as fast adaptation to new fuzzing problems.
- Distributing input data between the fuzzer processes for more effective work.
- Estimating severity for the crashes found.
- Using the Radamsa fuzzer for new input data generation.
- Automated fuzzing wrappers generation.
- Supporting various instrumentation tools such as DynamoRIO, QemuUserMode, GCC or LLVM static instrumentation, QemuSystemArm.
Sydr, a dynamic symbolic execution tool
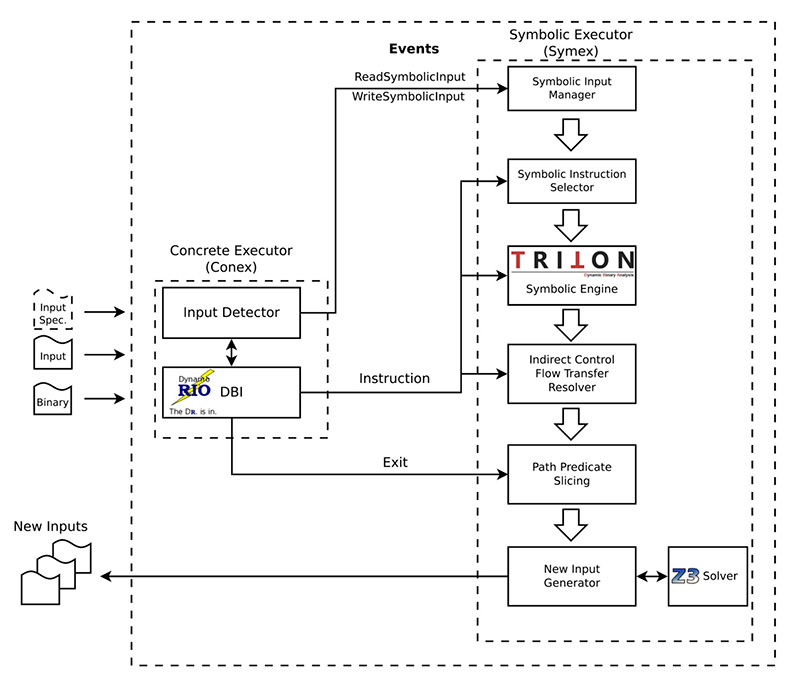
Sydr is an automatic test generation tool for complex programs that finds errors and increases code coverage during testing. Sydr constructs the program’s mathematical model that allows a fuzzer to explore new execution paths that are hard to follow via genetic mutation approaches. The tool advances further the dynamic symbolic execution approach used earlier in Avalanche and Anxiety analyzers developed in ISP RAS. In contrast with similar open source tools, Sydr ensures the correctness of generated input data by checking whether the newly found execution path has the target conditional branches inverted.
Sydr provides:
- Given an execution path, inverting all conditional branches that depend on input data. Inverting in parallel is also supported.
- ISP Fuzzer integration to reach the code behind the branches depending on comparisons with constants.
- Automating reverse engineering such as assisting an expert in reaching a given program point or collecting a trace of instructions that depend on input data.
- Supporting various input data sources (files, network sockets, environment variables, standard input stream, command line arguments).
- Safety predicates that are used to find errors and to generate input data for the errors found (for division by zero, null pointer dereference, buffer overflow).
- Symbolic execution of multithreaded programs.
- Inverting indirect branches (in switch statements). Table jumps and computed jumps are detected.
- Formula slicing. Sydr removes excessive formulae (not influencing the conditional branch being inverted) from the path predicate. This feature solves the problem of undertainting and speeds up SMT solver work for generated queries.
Who is ISP Crusher target audience?
- Companies developing highly reliable and secure software.
- Companies auditing or certifying software.
System requirements
Linux and Windows OS family support. Crusher can also fuzz embedded devices (controllers, IoT devices) as well as Windows services and COM objects.
ISP Crusher deployment stories
ISP Crusher is used in more than 40 companies and certification labs, including RusBITech, Postgres Professional, Security Code, Swemel and others.
ISP Crusher workflow
Sydr
Developer/Participant
Back to the list of technologies of ISP RAS 


